Which of the Following Is True About a Vpn
The DfltGrpPolicy group policy will be applied to any. The user will be able to establish a connection by using any tunnel group.
A VPN connection utilizes private networks instead of the public network.

. Which of the following is true of a VPN connections. Select the best answer The user will be unable to establish a VPN connection by using the boson tunnel group. Updated 792014 102148 PM.
Which of the following is a type of vpn connection. What Is True About A Virtual Private Network Vpn. A VPN network does not provide users with remote access.
Which statements are true of IPSec. An important benefit of using VPN over SSLTLS is that the source IP address in the protocol header of a. It provides a secure connection for information transmitted over the public Internet.
It is a network that uses a public telecommunication infrastructure such as the Internet. The VPN name may be dictated by your organizations naming conventions. It is an open standard protocol framework that is used to secure end-to-end communications.
If you are using VPN over SSLTLS there are two levels of encryption applied to the body of the packets sent to a destination computer by a source computer. IPsec is a security framework that provides security for data traveling over VPNs so this is a true statement. Which of the following statements are true about a virtual private network VPN.
Vpn is used to access which cloud mcq. Asked 792014 84917 PM. Have more security vulnerabilities than software VPNs.
An online service provider provides its users with hosted computers an operating system and a database management system DBMS. A VPN client software encrypts messages to ensure transmissions. A VPN connection appears as a secure connection though it is not.
Select the best answer The user will be unable to establish a VPN connection by using the boson tunnel group. Best when all router and firewall hardware is the same. Whichof the following is NOT a factor a secure VPN design should address.
It is an open standard protocol framework that is used to secure end-to-end communications. The computer acts as a. IPsec is a security framework that provides security for data traveling over VPNs so this is a true statement.
Data sent through a virtual private network vpn can be encrypted using the _____. Which of the following statements is true about the VPN in Network security. A virtual private network VPN extends a private network across a public network such as the Internet.
A VPN is a method of securing private data over public networks such as the Internet so this is a true statement. Log in for more information. The SSLTLS protocol encrypts only the body of a packet sent to a destination computer by a source computer.
1It can encryptdecrypt IP traffic only 2It can be used for authentication 3It can be used for Layer 2 VPN protocol. 1IPSec header is inserted between IP and Lower layer header 2IPSec header is inserted between IP and Upper layer header 3There is no IPSec header 4Only Authentication header is inserted 5Only Encapsulating Security Payload is. It typically creates a secure encrypted virtual tunnel over the open internet It is a type of device that helps to ensure that communication between a device and a network is secure.
The user will be able to establish a connection by using any tunnel group. Using this method you will disguise. Which of the following is true of a VPN connection.
Which of the following statements is true regarding VPN connections made by a user who is using the john user account. Each correct answer represents a complete solution. With a VPN connection you maintain a physical connection to the internet enabling you to stay secure.
A VPN is a method of securing private data. It is usually based on the IPsec IP Security or SSL Secure Sockets Layer. Which of the following statements is true regarding VPN connections made by a user who is using the john user account.
Which of the following is NOT true about a hardware VPN. The VPN name should not be identifiable. The VPN name should be redundant not unique in your Network and Sharing Center.
Which of the following is true about software VPNs. Choose all that apply. By using it you can keep your online activities private by masking your internet protocol address.
By default FortiGate uses WINS servers to resolve names. Tunneling is the process by which VPN packets reach their destination which is usually a private network. Which of the following is true of a virtual private network VPN.
Packets are encapsulated in Frame Relay frames and assigned Data Link Connection Identifiers DLCIs to identify to the local Frame Relay switch the virtual circuit VC that the data should follow. VPN uses tunneling to transfer data securely on the internet. The IPsec protocol suite is used by many VPNs.
The computer containing the VPN connection is actually connected to the network C. It does not require an IP addressThe computer containing the VPN connection is actually connected to the networkThe computer acts as a dumb terminalData does not traverse the Internet. Which of the following is true about a VPN.
A VPN is a method of securing private data over public networks such as the Internet so this is a true statement. The VPN enables you to transport all your data traffic through an encrypted tunnel. True A VPN is a secure encrypted connection that is established over a publicly shared network.
Traffic in a vpn is not _____ Traffic in a vpn is not _____. Which of the following statements is true regarding SSL VPN settings for an SSL VPN portal. Which of the following is true of a virtual private network vpn.
It does not require an IP address B. Frame Relay is a Layer 2 VPN technology providing connectivity over switched carrier Wide Area Networks WANs. Which of the following is true of VPN.
Using a VPN you can create a private network from a public internet connection to protect your online privacy. It operates at the Physical layer of theOSl model. The VPN name should not.
Asked Nov 1 2019 in Computer Science Information Technology by Iamxavier. A point to point vpn is also known as a. Which one is true of the Transport mode in IPSec.

Avast Secureline Vpn Review Techradar Check More At Https Alharo Com Avast Secureline Vpn Review Techradar

Wireguard Vpn Typical Setup The Poetry Of In Security

The Rise In Vpn Usage Infographic Virtual Private Network Private Network Infographic

Vpn Icon In Black Virtual Private Network Vector Eps 10 1051390 Icons Design Bundles In 2022 App Icon Design Virtual Private Network Icon

Vpn Connection What Is It And Why Do You Need One

Best Vpn Service Best Vpn Digital Marketing Solutions Marketing Software

Pin By Mill On Me Created Things So True Cancer True

How A Vpn Virtual Private Network Works Howstuffworks

Ikev2 Vpn Blackberry Devices Best Vpn Cellular Network

Vpn Explained How Does Vpn Work And Why Would You Use It

Nordvpn Logo Black Background Best Vpn Reviews Black Backgrounds

How To Setup L2tp Setup Osx Apps That Pay

Vpn All Computer Desktop Wallpaper Downloads In 2021 Virtual Private Network Private Network Best Vpn

Free Vietnam Vpn Best Vpn Vietnam Freedom Of Speech
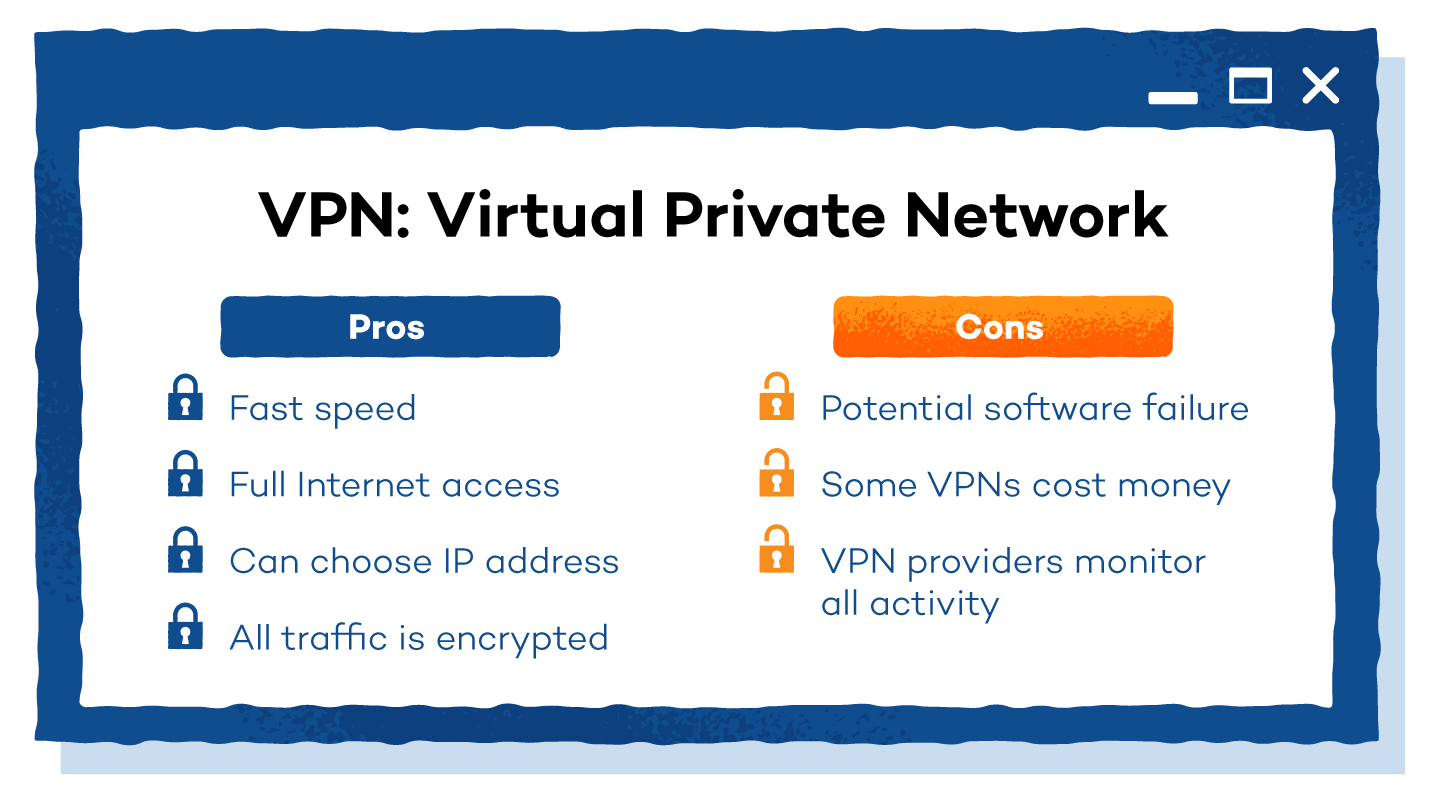
Tor Vs Vpn What They Do And Which Is Better Panda Security
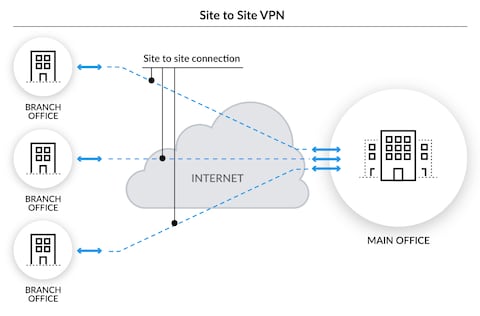
What Is A Site To Site Vpn Palo Alto Networks

Update Why You Want To Use A Vpn Digital Mar Virtual Private Network Best Vpn Business Networking


Comments
Post a Comment